Category: Security
IDA Debugger: you don’t have the necessary privileges.
during reverse engineering session, I encountered error from IDA saying “The debugger could not attach to the selected process. This can perhaps indicate the process was just terminated, or that you don’t have the necessary privileges.” I was debugging a 64-bit console application under WinDBG, and I did start IDA as Administrator, but it still
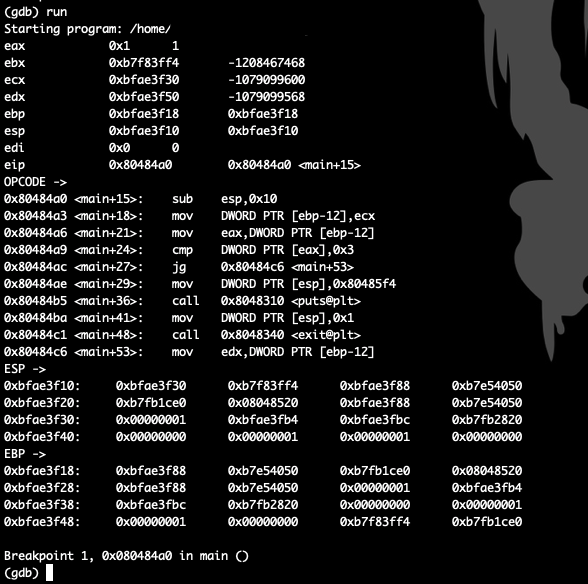
GDB hook .gdbinit
GDB hook that helps without third-party apps
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
set disassembly-flavor intel define hook-stop info register eax info register ebx info register ecx info register edx info register ebp info register esp info register edi info register eip echo OPCODE ->\r\n x/10i $pc echo ESP ->\r\n x/16w $esp echo EBP ->\r\n x/16w $ebp end |
audit keystrokes with pam
The pam_tty_audit PAM module is used to enable or disable TTY auditing. By default, the kernel does not audit input on any TTY this module is part of auditd and it takes 3 parameters 1 – disable is a pattern to disable the module in specified users u can use =* to disable it globally
Protect Boot & Single user mode
as a physical security is the main factor in our security perspective we all need to protect unauthorised access to our Linux box after we protect bios and we all know that anyone can rest the root password via accessing the single mode so we have 3 ways 1st thing to disable single user mode entirely
Secure/Lock accounts with PAM tally2
pam_tally2 is a PAM module to allow interaction in users interfaces on numbers of failed login attempt it can reset count on success, can deny access if too many attempts fail. this module is unique because it not just reflect remote connection but also reflect the ttys and any system login method as it uses PAM example
password policy with pam_cracklib
cracklib pam module is a method to check the password against dictionary list and gives you availability to check the strength of the password and set rules to identify the poor passwords here is the most important parameters for this module minlen minimal password length dcredit maximum number of digits ucredit maximum uppercase letters
Pluggable Authentication Modules
Linux comes with Pam Modules to help you to interact with the running services in hardening way and custom the security of the service as you need. PAM is extra Rules to Control user interfaces ( Auth, Account, Session) layers for the applications the applications/services should be compiled with libpam.so here is an example for
AIDE : Intrusion Detection Environment
this article about Intrusion Detection for file system changes like modification changing owner extra, for critical files or directories in our environment we using a software called AIDE Advanced Intrusion Detections Environment this software base on a library called mhash this lib used to calculate file hashes and AIDE save the file info inside DB
Google Drive Information Leak
Google Drive & Gmail attachments Leak This part of Google bounty program [IDOR] exploit to allow the attacker to leak your Google Drive files and this mean attacker could leak Gmail attachments that uploaded to Google Drive, Photos you shared with Gmail or any other third party
removable disk could lead to privilege escalation
privilege escalation Linux with flash disk removable media with setUID, setGID files could give privilege escalation example copy nice command to ur flash storage and ask ur friend to print files in his system then run the command nice like
|
1 |
nice whoami |
it will say root the problem occurs from a mounted partition without noexec,nosuid parameter