Category: Uncategorized
Jump between domains – Enterprise Admins Golden Ticket
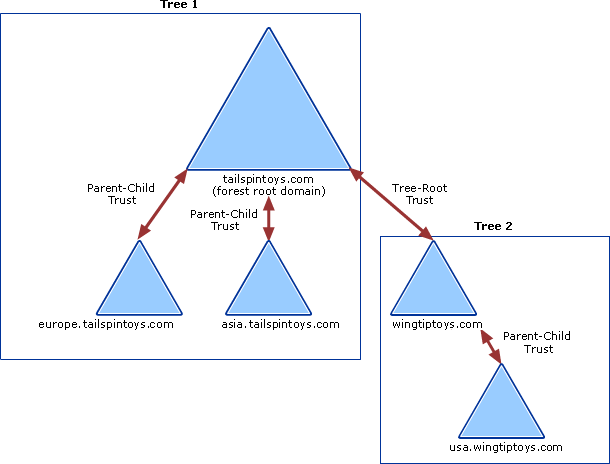
How to take over all the domains. But let’s add a quick recap first. To build an active directory domain, you start with a root domain, for example, UNIXAWY.CORP, which is the root domain/company, then you start a new branch or merge and acquisition a new company, then you want to extend your network for
Shellcode validation via C pointer
C snippet to test the shellcode replace your shellcode with your custom payload
|
1 2 3 4 5 6 7 |
char shellcode[] = "\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc"; int main(int argc, char **argv){ int (*target)(); target = (int(*)())shellcode; (int)(*target)(); } |
phpMyAdmin error #1146
#1146 – Table ‘phpmyadmin.pma_tracking’ doesn’t exist this error indicates that phpmyadmin pages failed in setup and you just ignored it in the setup process you need to reconfigure the package again
|
1 |
root@ubuntu:~# dpkg-reconfigure phpmyadmin |
after you follow the reinstall steps it will setup the missing sql files for pma tables
Regex to find mac address
today i was doing some forensics to find mac address inside syslog in linux systems i wrote this simple grep command to filter mac address from log files grep ‘[0-9a-zAz]\{2\}:[0-9a-zAz]\{2\}:[0-9a-zAz]\{2\}:[0-9a-zAz]\{2\}:[0-9a-zAz]\{2\}:[0-9a-zAz]\{2\}’ have fun
find duplicated UID in the linux system
u can identify the duplicated uid in your system this useful to identify if there some manipulation inside the users’ accounts getent passwd|cut -d : -f3 |sort -n|uniq -d it only returns the duplicated uid btw: if it returns 0 😀 you know the rest
underc0de 3 WalkThrough
loaded the virtual machine and run netdiscover to get the machine IP
|
1 2 3 4 5 6 7 8 9 10 11 |
oot@n1x:~# netdiscover Currently scanning: 192.168.39.0/16 | Screen View: Unique Hosts 4 Captured ARP Req/Rep packets, from 4 hosts. Total size: 240 _____________________________________________________________________________ IP At MAC Address Count Len MAC Vendor ----------------------------------------------------------------------------- 192.168.1.1 e8:94:f6:5d:c6:3b 01 060 Unknown vendor 192.168.1.2 00:18:fe:6d:61:27 01 060 Hewlett Packard 192.168.1.100 6c:40:08:98:68:d4 01 060 Unknown vendor 192.168.1.112 00:0c:29:fb:62:53 01 060 VMware, Inc. |
x.112 is the target so let’s see what ports available
|
1 2 3 4 5 6 7 8 9 10 11 12 |
root@n1x:~# nmap -sSV -p1-9999 192.168.1.112 Starting Nmap 6.47 ( http://nmap.org ) at 2014-12-01 02:49 EST Nmap scan report for 192.168.1.112 Host is up (0.00019s latency). Not shown: 9996 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 6.0p1 Debian 4+deb7u2 (protocol 2.0) 25/tcp open smtp Postfix smtpd 80/tcp open http Apache httpd 2.2.22 ((Debian)) MAC Address: 00:0C:29:FB:62:53 (VMware) Service Info: Host: Underdist; OS: Linux; CPE: cpe:/o:linux:linux_kernel |
apache is on 😀 so let’s brute-force the directory in the server
Hello world!
Welcome to UNIXAWY. This is my first post. I made the blog to save someone time as someone saved my time 😉